3 Ways to Protect Your Home from Cyber Threats
IT PROJECTS
5/10/20256 min read


By now we know how cyber threats pose serious risks to individuals and families, impacting everything from personal data to financial security. I have seen firsthand how cyber threats infiltrate home networks and exploit the people and information within a home Wi-Fi network. Let’s take a look at some security measures we can take to protect ourselves and our families.
How to Secure Home Networks
Take for example a typical baby monitor installed in the home, have you ever wondered why so many baby monitors advertise that they purposely do not include Wi-Fi capability when seemingly most electronic devices we have in our homes are Wi-Fi compatible? It is because baby monitors with Wi-Fi capability are vulnerable to being hacked, and parents worry that someone could be spying on their baby or worse. But if we are so concerned with protecting our baby from the dangers of an unsecured wireless smart device like a baby monitor, why don’t we care about securing all of our other IoT/home network devices from compromise? Protecting your home Wi-Fi and internet traffic is crucial for online safety, just as safeguarding children in the physical world is a parental responsibility. Below are some ways you can secure your family’s online activity at home:
1. Anti-Virus
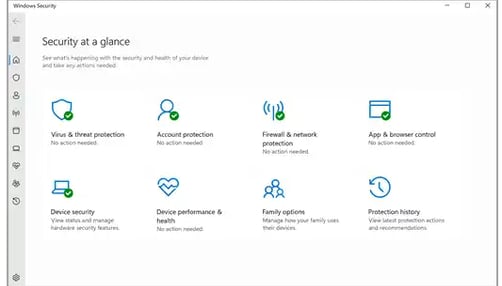
Windows Defender: Built-in Antivirus Protection
Windows Defender provides real-time threat detection and scanning integrated into the Windows OS. Independently tested by AV-test.org, it achieves high scores for protection, performance, and usability.
Designed for continuous system security, Windows Defender runs automatically and requires replacement by another antivirus solution for deactivation. This mandatory protection reflects Microsoft's stance on the critical need for antivirus software on Windows systems.
While core functionality remains always-on, specific features like Real-time Protection and Tamper Protection can be disabled. This may be necessary for troubleshooting performance issues, such as slow network file transfers potentially caused by real-time scanning. Performance optimization can also be achieved by configuring exclusions for specific files, folders, or application temporary/cache directories within Windows Defender.
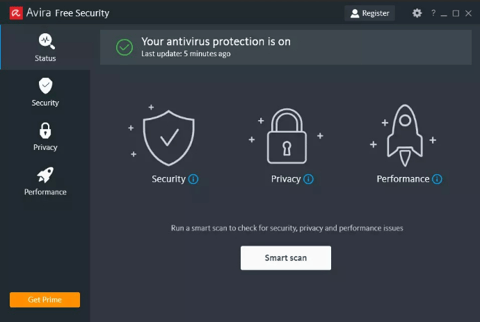
Avira Free Security: All In One Protection
Avira Free Security provides comprehensive Windows and Mac protection against malware and viruses, incorporating internet security, online privacy, and performance optimization features. Independently tested by AV-test.org, Avira achieves high scores in protection, performance, and usability. The Smart Scan feature facilitates a single-click system check across these areas. The free edition also includes a VPN with a 500MB monthly data allowance. In seven years of personal use across multiple home devices, Avira has consistently and effectively identified and quarantined threats, preventing any system compromise.
2.Harden Operating Systems
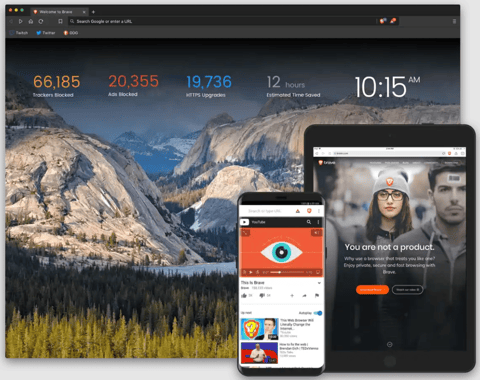
Brave Browser: A secure, private Internet browser
The Brave browser is awesome. It is a free open-source web browser based on Chromium. First of all, it quite fast and responsive compared to traditional browsers like Microsoft Edge, Google Chrome, and Safari. It blocks third-party ads on every single website by default, no additional browser extensions needed. Brave is paired with a built-in VPN that users can access by purchasing a Brave Firewall + VPN subscription for $9.99/month which protects up to 10 devices.
VMware Workstation Pro: To test sketchy links or software
For safe software testing and experimentation, a software-based hypervisor like VMware Workstation Pro allows creation of isolated virtual machines. This prevents experimental software, including malware, from affecting the host system. Snapshots enable reverting the virtual machine to a prior state, ensuring a clean environment for each test.


DuckDuckGo: A private search engine that won’t collect personal information
An alternative to Google and Bing, DuckDuckGo protects privacy by not tracking your input and blocks third-party tackers. This can reduce the risk of personal information getting leaked to unauthorized entities.


VeraCrypt: File and Disk Encryption Software that protects data in case you lose your computer or laptop
VeraCrypt is a free tool that creates a secure, encrypted "vault" on your computer or a USB drive. Imagine a strongbox that you can put files into. You lock the strongbox with a password (and/or keyfiles), and nobody can open it without the correct combination.
VeraCrypt takes this a step further by making the entire strongbox invisible unless you "unlock" it. To others, it just looks like free space on your drive.
Why is this useful?
· Protects sensitive data: If your computer is lost or stolen, the thief can't access the encrypted files even if they take out the hard drive.
· Privacy: Keeps your personal information private, even if someone has physical access to your device.
· Security: Safeguards against malware that tries to steal your data.
· Portable security: You can create encrypted containers on USB drives to carry your sensitive data securely.
Essentially, VeraCrypt provides a powerful layer of security for your important files, offering peace of mind in a world with increasing digital threats.


KeePass: Password manager to protect passwords from being stolen, compromised, and lost
Free open source password manager, stores all of your passwords in one central location that is encrypted, users only need to remember one password to access their password data.


Windows Update: Keeps your Windows OS updated and reduces security vulnerabilities
Not much to say here, just keep your Windows computers up to date.
ExpressVPN: Virtual Private Network masks your IP address to prevent location tracking and improve anonymity online.
An easy to use way to help prevent cyber attacks is to use a VPN. A VPN is an encrypted private tunnel that exists between you and the websites you visit, it doesn't allow tracking, intercepting, or snooping from outside entities and keeps your activity anonymous. I've been using ExpressVPN as they allow up to 8 devices be used at once and support all platforms including Android, iPhone, Windows, Linux, and more.


3.Securing IoT Devices on Home Wi-Fi
Change the default credentials for home Wi-Fi SSID.
Tip: Don’t include your name, address, or any personal information when renaming your SSID, this only broadens your attack surface.
Change the default credentials on all IoT devices
Tip: Anyone can google the default username and password for Ring cameras, it is the same for every device. If someone gains access to your IoT devices, they can login and compromise them from anywhere.
Limit IoT devices to communicate using only required ports and protocols
Tip: IP connected devices communicate using specific ports and protocols, many IoT devices have more open ports than necessary listening on them and more protocols running than necessary. Hackers can exploit open ports and protocols to compromise systems using tools like NMAP. Close down unnecessary open ports and disable unnecessary protocols to reduce attack surface.
Use a firewall to block unnecessary connections to/from IoT devices
Tip: IoT devices are often vulnerable due to limited security features, default passwords, and infrequent updates. A firewall can act as a crucial layer of defense, most home routers have a built-in firewall that can be configured or you can purchase a dedicated firewall device or you can repurpose old hardware (such as an old PC) to run software-based a firewall. One of the most trusted and most used firewalls (especially for home users) is an open-source software-based firewall called pfSense. See how you can install it for use on your home network here.
Some firewall rules of thumb include:
Block Unnecessary Connections: Create rules to block outbound connections to any IPS or ports that are not required such as known advertising servers or data collections services.
Block Inbound Connections: Most of the time, IoT devices don't need to accept inbound connections from the internet except possibly for remote access, blocking these connections will significantly reduce the attack surface of your devices.
Destination Port Filtering: Block connections to specific ports that are not needed or inherently insecure (such as Telnet on port 23)
Example of a basic firewall rule:
Rule (Block All Inbound Traffic):
Source IP: Any
Destination IP: 192.168.1.50
Destination Port: Any
Protocol: TCP/UDP
Action: Deny
Segment home network traffic using subnets
This is optional, but I do this at home because I have a separate home lab domain.
Scan your home devices for vulnerabilities
Tip: Secure your home network with a free vulnerability scan using Nessus Essentials. While limited to 16 IP addresses, it can identify weaknesses in your computers and IoT devices. Note that some advanced features are exclusive to the paid version. Begin by registering for a free activation code, then download and install the Nessus Essentials scanner.
It's free, but limited to 16 IP addresses per scanner.
It doesn't support unlimited scanning, compliance checks, content audits, Live Results, configurable reports, or the Nessus virtual appliance.
Technical support is not available for Nessus Essentials
